Identifying the Person Behind Bitcoin Fog
Schneier on Security
MAY 3, 2021
The complaint outlines how Sterlingov allegedly paid for the server hosting of Bitcoin Fog at one point in 2011 using the now-defunct digital currency Liberty Reserve.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
MAY 3, 2021
The complaint outlines how Sterlingov allegedly paid for the server hosting of Bitcoin Fog at one point in 2011 using the now-defunct digital currency Liberty Reserve.

The Hacker News
NOVEMBER 8, 2024
The 36-year-old founder of the Bitcoin Fog cryptocurrency mixer has been sentenced to 12 years and six months in prison for facilitating money laundering activities between 2011 and 2021.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JUNE 20, 2018
Cryptojacking, as defined by the Federal Trade Commission , is the use of JavaScript code to capture cryptocurrencies in users’ browsers without asking permission. LW: So cryptocurrency got discovered as the ideal payment vehicle for ransomware. In 2011, total cryptocurrency value was about $10 billion. Bilogorskiy.

CSO Magazine
OCTOBER 25, 2022
According to data from the Rekt leaderboard , cybercriminals have stolen as much as $3 billion of investor funds through 141 various cryptocurrency exploits since January, putting 2022 on track to top 2021 levels of digital currency malfeasance. Comparitech’s cryptocurrency heists tracker indicates that since 2011, hackers have stolen $7.9

The Hacker News
MAY 7, 2024
A Russian operator of a now-dismantled BTC-e cryptocurrency exchange has pleaded guilty to money laundering charges from 2011 to 2017. Alexander Vinnik, 44, was charged in January 2017 and taken into custody in Greece in July 2017. He was subsequently extradited to the U.S. in August 2022.

Security Affairs
FEBRUARY 6, 2024
A Belarusian and Cypriot national linked with the cryptocurrency exchange BTC-e is facing charges that can lead maximum penalty of 25 years in prison. “According to the indictment, between 2011 and July 2017, Aliaksandr Klimenka, 42, allegedly controlled BTC-e, a digital currency exchange, with Alexander Vinnik and others.”
Krebs on Security
MAY 13, 2024
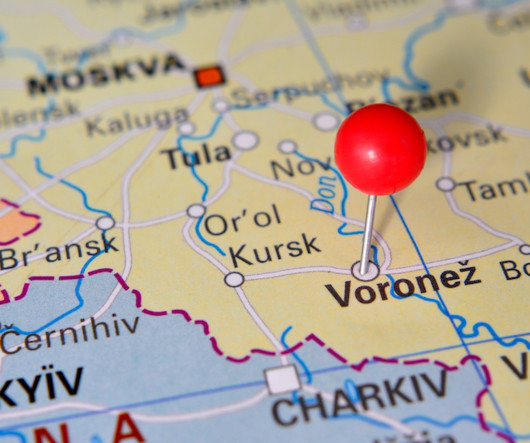
NEROWOLFE A search on the ICQ number 669316 at Intel 471 shows that in April 2011, a user by the name NeroWolfe joined the Russian cybercrime forum Zloy using the email address d.horoshev@gmail.com , and from an Internet address in Voronezh, RU. 2011 said he was a system administrator and C++ coder.

Security Affairs
JUNE 9, 2023
Two Russian nationals have been charged with the hack of the cryptocurrency exchange Mt. Gox in 2011 and money laundering. Russian nationals Alexey Bilyuchenko (43) and Aleksandr Verner (29) have been charged with the hack of the cryptocurrency exchange Mt. Then the attackers transferred funds from Mt. ” reads the DoJ.

Bleeping Computer
JUNE 9, 2023
Russian nationals Alexey Bilyuchenko and Aleksandr Verner have been charged with the 2011 hacking of the leading (at the time) cryptocurrency exchange Mt. Gox and the laundering of around 647,000 bitcoins they stole. [.]

Malwarebytes
APRIL 6, 2022
It was rife during the earthquake and tsunami of 2011 , with bogus Red Cross websites and email addresses set up to part people from their money. The tactics used match those deployed in 2011, and pretty much every other major catastrophe. Cryptocurrency scamming is rampant. The lowest of the low. Fake it to make it.

The Hacker News
JUNE 13, 2023
Department of Justice (DoJ) has charged two Russian nationals in connection with masterminding the 2014 digital heist of the now-defunct cryptocurrency exchange Mt.

Security Affairs
JANUARY 2, 2022
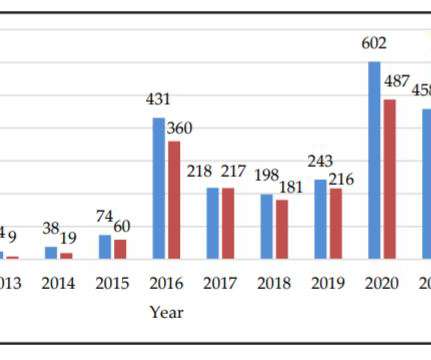
The cyberattacks against the cryptocurrency industry are a profitable business for threat actors, according to the experts, $12.1 billion worth of cryptocurrencies have been stolen in the last decade. “Cryptocurrency crime stands in direct proportion to the size of the cryptocurrency market. Threat actors stole $3.18
Security Affairs
OCTOBER 16, 2021
FinCEN analyzed a data set composed of 2,184 SARs filed between 1 January 2011 and 30 June 2021 and identified 177 CVC (convertible virtual currency) wallets addresses that were used in ransomware operations associated with the above ransomware variants. Follow me on Twitter: @securityaffairs and Facebook.

Security Affairs
MAY 6, 2024
Alexander Vinnik , a Russian national, pleaded guilty to conspiracy to commit money laundering for his involvement in operating the cryptocurrency exchange BTC-e from 2011 to 2017. charged Aliaksandr Klimenka, a Belarusian and Cypriot national linked with the cryptocurrency exchange BTC-e. reported the Associated Press.

Security Affairs
JUNE 22, 2020
In September, Greek Police have arrested the Russian national Alexander Vinnik (38) and they accuse the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency. The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 million withdrawn.

Security Boulevard
JUNE 12, 2023
Bilyuchenko and Verner are charged with conspiring to launder approximately 647,000 bitcoins from the 2011 hack of Mt. Bilyuchenko is separately charged with conspiring with Alexander Vinnik to operate the illicit cryptocurrency exchange BTC-e from 2011 to 2017.

Security Affairs
OCTOBER 19, 2020
In 2017, Greek Police arrested the Russian national Alexander Vinnik and they accused the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency. The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 million withdrawn.

Bleeping Computer
MARCH 13, 2024
for operating Bitcoin Fog between 2011 and 2021. [.] Russian-Swedish national Roman Sterlingov was convicted by a federal jury in Washington, D.C.,
Security Affairs
DECEMBER 7, 2021
The blockchain-enabled botnet has been active since at least 2011, researchers estimate that the Glupteba botnet is currently composed of more than 1 million Windows PCs around the world.

Security Affairs
DECEMBER 8, 2020
In 2017, Greek Police arrested the Russian national Alexander Vinnik and they accused the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency. The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 million withdrawn. Pierluigi Paganini.
Security Affairs
OCTOBER 26, 2020
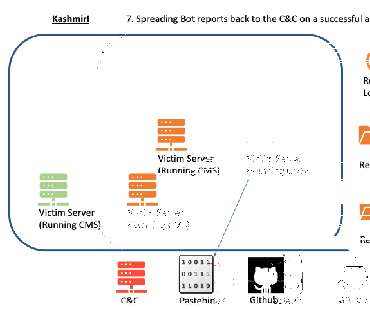
The primary purpose of the KashmirBlack botnet is to abuse resources of compromised systems for cryptocurrency mining and redirecting a site’s legitimate traffic to spam pages. .” reads the first part of two reports published by the experts detailing the DevOps implementation behind the botnet.

Security Affairs
MAY 30, 2024
Since 2011, Wang and his co-conspirators had been distributing malware through malicious VPN applications, including MaskVPN, DewVPN, PaladinVPN, ProxyGate, ShieldVPN, and ShineVPN. The law enforcement also arrested its administrator, the 35-year-old Chinese national YunHe Wang, in Singapore. ” reads the press release published by DoJ.

Security Affairs
APRIL 28, 2023
The malware allows operators to steal login credentials from popular services such as social media platforms and cryptocurrency wallets, then stolen data is sold on cybercrime forums by the operators. CryptBot malware is active since at least 2019, it allows operators to steal sensitive data from the Google Chrome of the infected systems.
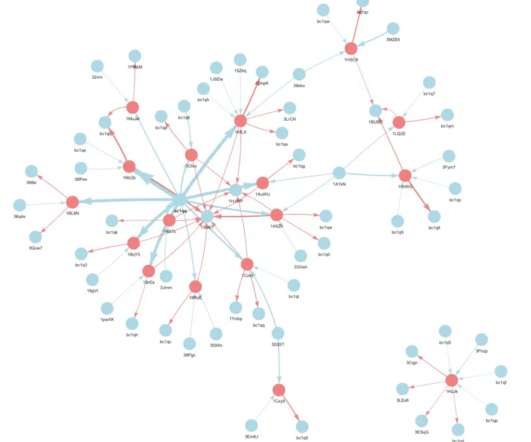
Security Affairs
DECEMBER 19, 2022
The blockchain-enabled botnet has been active since at least 2011, researchers estimated that the Glupteba botnet was composed of more than 1 million Windows PCs around the world as of December 2021.

Webroot
MAY 12, 2021
“What Bitcoin was to 2011, NFTs are to 2021.”. Since cryptocurrencies were, are and will continue to be impactful technologies, surely NFTs are a topic worth exploring. NFTs use the same blockchain ledger technology to verify uniqueness that cryptocurrencies rely on to prove ownership.

Security Affairs
NOVEMBER 6, 2020
“The seizure represents the largest seizure of cryptocurrency in the history of the Department of Justice.” filed a civil complaint to forfeit the funds, this is the largest seizure of cryptocurrency funds the Department of Justice has ever made. .” reads the press release published by the DoJ.

Security Affairs
SEPTEMBER 17, 2018
Greek Police have arrested the Russian national Alexander Vinnik (38) and they accuse the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency. The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 million withdrawn.

Identity IQ
FEBRUARY 8, 2024
Transactions on the dark web are typically conducted using cryptocurrencies such as Bitcoin to maintain anonymity. Transactions on the dark web are often carried out with Bitcoin or other cryptocurrencies, which are unregulated and difficult to trace back to the user. From 2011 to 2013, the Silk Road hosted 1.2 billion in value.

SecureList
SEPTEMBER 26, 2022
SmokeLoader (aka Smoke) is a modular malware that has been known since 2011, distributed via phishing emails and drive-by downloads. RedLine’s main purpose is to steal credentials and information from browsers, in addition to stealing credit card details and cryptocurrency wallets from the compromised machine. SmokeLoader.
SecureList
NOVEMBER 29, 2024
Tropic Trooper spies on government entities in the Middle East The threat actor Tropic Trooper, active since 2011, has historically targeted government, healthcare, transportation and high-tech sectors in Taiwan, the Philippines and Hong Kong.

Security Affairs
DECEMBER 21, 2019
In September, Greek Police have arrested the Russian national Alexander Vinnik (38) and they accuse the man of running the BTC-e Bitcoin exchange to launder more than US$4bn worth of the cryptocurrency. The authorities reported that since 2011, 7 million Bitcoin went into the BTC-e exchange and 5.5 million withdrawn.

Security Affairs
SEPTEMBER 2, 2018
. · Iran-linked COBALT DICKENS group targets universities in new phishing campaign. · Security firm attributes Cosmos Bank cyberheist to Lazarus APT. · Cryptocurrency Platform Atlas Quantum hacked, 260k users impacted. · CVE-2018-15919 username enumeration flaw affects OpenSSH Versions Since 2011. · Data of 130 Million hotel (..)

SecureWorld News
APRIL 29, 2021
The Department of Justice (DOJ) describes his crimes like this: "Bitcoin Fog was the longest-running cryptocurrency 'mixer,' gaining notoriety as a go-to money laundering service for criminals seeking to hide their illicit proceeds from law enforcement. Over the course of its decade-long operation, Bitcoin Fog moved over 1.2

eSecurity Planet
SEPTEMBER 14, 2022
One particularly potent emergent technology for scammers is blockchain and the related cryptocurrency and NFTs. This variant of fraud has been around since at least 2011, when an Australian Broadcasting Corporation employee with high-level IT access privileges hijacked company computers to mine Bitcoin.

Security Affairs
AUGUST 8, 2018
Ramnit is one of the most popular banking malware families in existence today, it was first spotted in 2010 as a worm, in 2011, its authors improved it starting from the leaked Zeus source code turning the malware into a banking Trojan. DDoS attacks, ransomware-based campaigns, cryptocurrency mining campaigns).
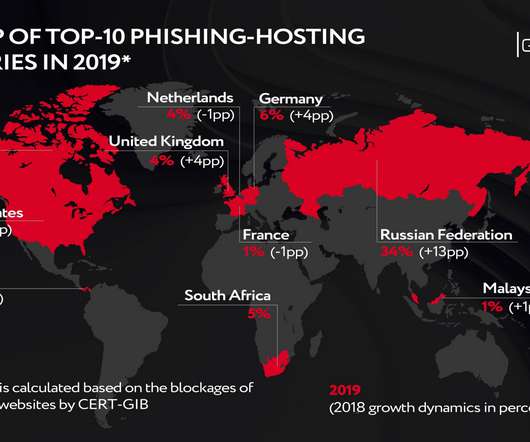
Security Affairs
MAY 8, 2020
About CERT-GIB CERT-GIB, opened in 2011, became the first certified private emergency response services in Eastern Europe and currently is one of the largest ones in the region. Balance of power. Figure 2 The map of major web phishing-hosting countries.
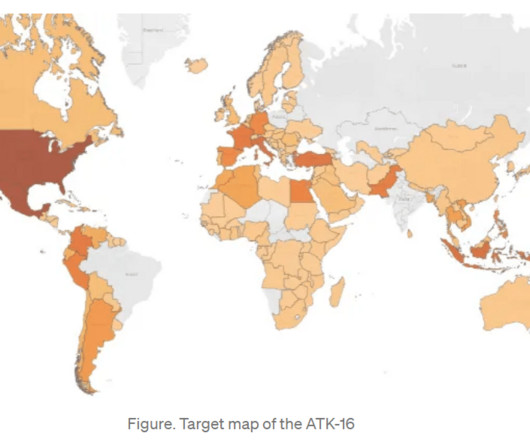
Security Affairs
MARCH 27, 2023
He is a former member of the ANeSeC CTF team, one of the firsts Italian cyber wargame teams born back in 2011. The module also exfiltrates 2FA secrets from Twilio’s Authy local storage.

DoublePulsar
MARCH 2, 2020
I finished Skyrim in 2011 and haven’t recovered yet). such as this one, spotted by the team I’ll be joining, where software was used to deliver rogue cryptocurrency miners. This is something Microsoft Threat Protection is leading the way on, and this is fundamentally why I started looking at this job. Me, by the way… like, badly?—?I

Elie
DECEMBER 20, 2018
Looking at the adoption of 2FA by site categories reveals that FINTECH- (financial technologies) and IT (information technology)-related services, such as cryptocurrency and cloud services, are leading the 2FA adoption charge. in 2011 almost 10 years ago. Support for various categories. HOTP was standardized in the.

ForAllSecure
MARCH 1, 2022
In 2011, there a was user in a chat room by the name of altoid, like the mint. Anyone talking about it in 2011 most likely had inside information. For that you're going to need cryptocurrency. Here's when you buy some cryptocurrency and set up a wallet. This is cryptocurrency laundering. And he had. You need a VPN.

SecureList
MARCH 1, 2021
It stole credentials for various financial systems including online banking applications and cryptocurrency wallets in Brazil. This is a typical example of the kind of old-school text-message scams that were popular in 2011 and 2012. The Trojan Ghimob was one of 2020’s most exciting discoveries.

Security Boulevard
JULY 2, 2024
IntroductionIn this two-part blog series, we explore the evolution of SmokeLoader, a malware downloader that has been active since 2011. CMD_MINER or CMD_EMPTY0x271ERequests a cryptocurrency miner executable from the server. They are separated by the substring {:!:}.CMD_MINER
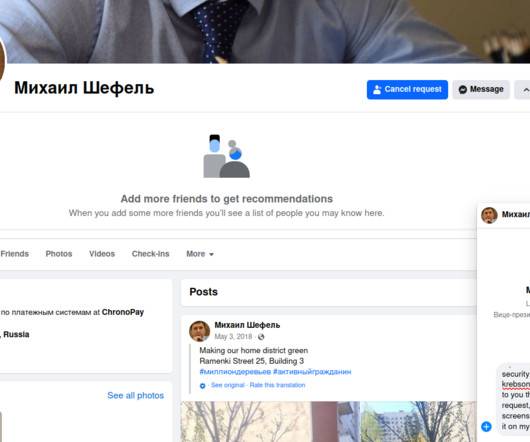
Krebs on Security
DECEMBER 14, 2023
Much of my reporting on Vrublevsky’s cybercrime empire came from several years worth of internal ChronoPay emails and documents that were leaked online in 2010 and 2011. me , which included a copyright credit to “Hot Spot 2011.” Pavel Vrublevsky’s former Facebook profile photo. WHERE ARE THEY NOW?

Security Affairs
JUNE 23, 2021
The company was purchased by Intel in 2011 for more than $7.6bn. According to the indictment , the expert earned millions in income from promoting cryptocurrencies, consulting work, speaking engagements, and selling the rights to his life story for a documentary.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content