More Detail on the Juniper Hack and the NSA PRNG Backdoor
Schneier on Security
SEPTEMBER 9, 2021
Here’s me in 2015 about this Juniper hack. Here’s me in 2007 on the NSA backdoor. We knew the basics of this story , but it’s good to have more detail.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
SEPTEMBER 9, 2021
Here’s me in 2015 about this Juniper hack. Here’s me in 2007 on the NSA backdoor. We knew the basics of this story , but it’s good to have more detail.
Krebs on Security
AUGUST 29, 2023
Emerging in 2007 as a banking trojan, QakBot (a.k.a. According to recent figures from the managed security firm Reliaquest , QakBot is by far the most prevalent malware “loader” — malicious software used to secure access to a hacked network and help drop additional malware payloads.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Affairs
FEBRUARY 22, 2025
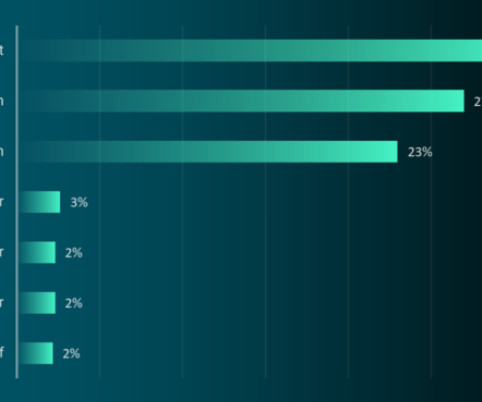
The Bybit hack is the largest cryptocurrency heist ever, surpassing previous ones like Ronin Network ($625M), Poly Network ($611M), and BNB Bridge ($566M). Bybit is Solvent even if this hack loss is not recovered, all of clients assets are 1 to 1 backed, we can cover the loss. billion to an unidentified address.
Krebs on Security
MARCH 10, 2020
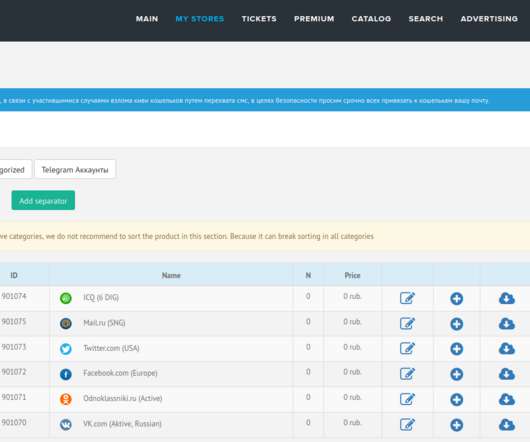
District Court for the Southern District of California allege Firsov was the administrator of deer.io, an online platform that hosted more than 24,000 shops for selling stolen and/or hacked usernames and passwords for a variety of top online destinations. It also was used in 2007 to register xeka[.]ru Click image to enlarge.

Security Affairs
DECEMBER 18, 2024
The Mask APT has been active since at least 2007, it demonstrated the capability to use complex implants, often delivered through zero-day exploits. ” Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs hacking,APT)

Krebs on Security
SEPTEMBER 17, 2020
Justice Department this week indicted seven Chinese nationals for a decade-long hacking spree that targeted more than 100 high-tech and online gaming companies. Security firm FireEye dubbed that hacking blitz “one of the broadest campaigns by a Chinese cyber espionage actor we have observed in recent years.” Image: FBI.
Krebs on Security
JUNE 1, 2023
Prior to that, akafitis@gmail.com was used as the email address for the account “ Fitis ,” which was active on Exploit between September 2006 and May 2007. ru in its early years, but for a brief period in 2007 it appears this website was inadvertently exposing all of its file directories to the Internet. ru in 2008.
Security Affairs
FEBRUARY 26, 2024
Recently the leak of a collection of files apparently stolen from the Chinese government hacking contractor, I-Soon, exposed Chinese hacking capabilities. Recently someone has leaked on GitHub [ 1 , 2 ] a collection of files apparently stolen from the Chinese hacking firm, I-Soon.

Security Affairs
OCTOBER 29, 2020
Russia-linked APT Turla has hacked into the systems of an undisclosed European government organization according to Accenture. According to a report published by Accenture Cyber Threat Intelligence (ACTI), Russia-linked cyber-espionage group Turla has hacked into the systems of an undisclosed European government organization.

WIRED Threat Level
OCTOBER 23, 2020
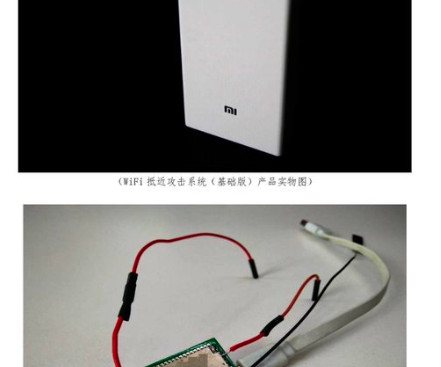
A secret experiment in 2007 proved that hackers could devastate power grid equipment beyond repair—with a file no bigger than a gif.

Security Affairs
SEPTEMBER 5, 2024
“Our office connection was hacked, and we are now taking protective measures.” The APT28 group (aka Fancy Bear , Pawn Storm , Sofacy Group , Sednit , BlueDelta, and STRONTIUM ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide.
Security Affairs
OCTOBER 27, 2021
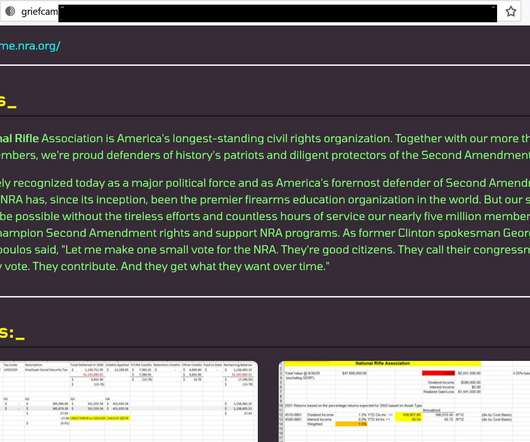
Grief ransomware operators announced to have hacked US National Rifle Association (NRA) and threaten to leak the stolen data. The NRA was added to the list of compromised organizations on the leak site of the group, that gang also published a set of documents as proof of the hack. SecurityAffairs – hacking, NRA).

Security Affairs
AUGUST 19, 2022
Undersecretary for Digital Transformation Luukas Ilves announced that Estonia was hit by the most extensive wave of DDoS attacks it has faced since 2007. Yesterday, Estonia was subject to the most extensive cyber attacks it has faced since 2007. SecurityAffairs – hacking, Estonia). Pierluigi Paganini.
Security Affairs
JUNE 21, 2023
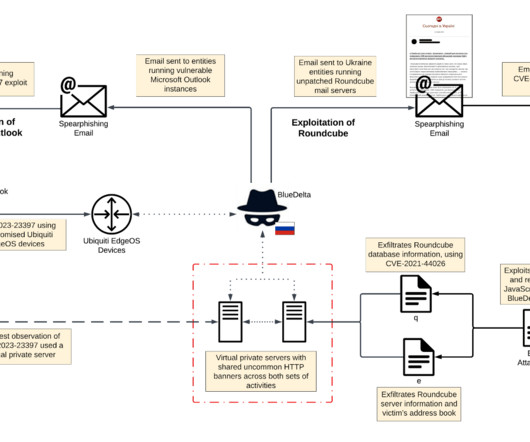
Russia-linked APT28 group hacked into Roundcube email servers belonging to multiple Ukrainian organizations. The APT28 group (aka Fancy Bear , Pawn Storm , Sofacy Group , Sednit , BlueDelta, and STRONTIUM ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide.

Security Affairs
NOVEMBER 10, 2018
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. The post Symantec shared details of North Korean Lazarus’s FastCash Trojan used to hack banks appeared first on Security Affairs.

Security Affairs
MARCH 9, 2020
Multiple state-sponsored hacking groups are attempting to exploit a vulnerability recently addressed in Microsoft Exchange email servers. A couple of weeks ago, the popular security researcher Kevin Beaumont reported mass scanning for the CVE-2020-0688 (Microsoft Exchange 2007+ RCE vulnerability). Pierluigi Paganini.
Security Affairs
JUNE 30, 2021
for his key role in the distribution of the Gozi virus that infected more than a million computers from 2007 to 2012. The Gozi banking Trojan is not a new threat, it was first spotted by security researchers in 2007. SecurityAffairs – hacking, Gozi ). Paunescu was arrested in Romania in 2012, but was able to avoid extradition.
Security Affairs
DECEMBER 6, 2020
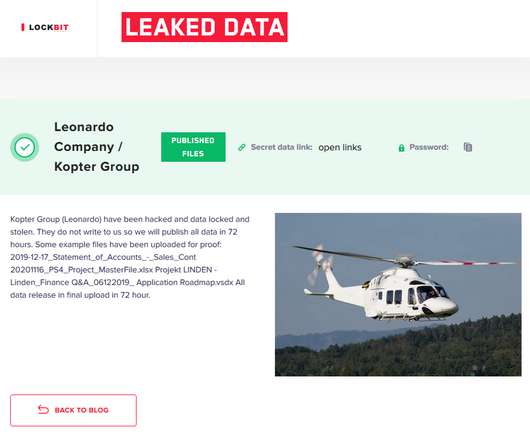
Kopter Group is Switzerland-based company that was founded in 2007 that was acquired by Leonardo in April 2020. SecurityAffairs – hacking, ransomware). The helicopter maker Kopter was hit by LockBit ransomware, the attackers compromised its internal network and encrypted the company’s files. ” reported ZDNet.

Security Affairs
JANUARY 11, 2021
court on Thursday sentenced the Russian hacker Andrei Tyurin to 12 years in prison for his role in an international hacking campaign. The man was arrested in Georgia at the request of US authorities, he was charged with multiple conspiracy counts, including wire fraud, aggravated identity theft and four counts of computer hacking.

Security Affairs
AUGUST 6, 2019
The STRONTIUM APT group (aka APT28 , Fancy Bear , Pawn Storm , Sofacy Group , and Sednit ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. SecurityAffairs – Russia APT, hacking). link] #MSFTatBlackHat — Security Response (@msftsecresponse) August 5, 2019.

Security Affairs
OCTOBER 21, 2021
The Evil Corp cybercrime group (aka the Dridex gang Indrik Spider , the Dridex gang, and TA505 ) has been active in cybercrime activities since 2007. 32) and Igor Turashev (38) for distributing the infamous Dridex banking Trojan , and for their involvement in international bank fraud and computer hacking schemes. Pierluigi Paganini.

Schneier on Security
JUNE 8, 2021
” It’s a similar attitude to corporate executives who believe that they can’t be hacked — and equally naive. Militaries around the world are now exploiting these vulnerabilities in weapons systems to carry out operations.

Heimadal Security
OCTOBER 22, 2021
About Evil Corp Also known as the Dridex gang or INDRIK SPIDER, the Russia-based hacking group Evil Corp has been around since at least 2007 and is notorious for developing and distributing […]. The post Macaw Locker, Evil Corp’s Latest Version Makes New Victims appeared first on Heimdal Security Blog.

Security Affairs
DECEMBER 28, 2019
Zynga Inc is an American social game developer running social video game services founded in April 2007, it primarily focuses on mobile and social networking platforms. The post 173 Million Zynga accounts were impacted in the September hack appeared first on Security Affairs. Pierluigi Paganini. SecurityAffairs – Zynga, data breach).

Quick Heal Antivirus
NOVEMBER 11, 2022
QBot, also known as Qakbot, QuackBot, and Pinkslipbot, is a Banking Trojan that was first observed in 2007. The post QBOT – A HTML Smuggling technique to target victims appeared first on Quick Heal Blog | Latest computer security news, tips, and advice.
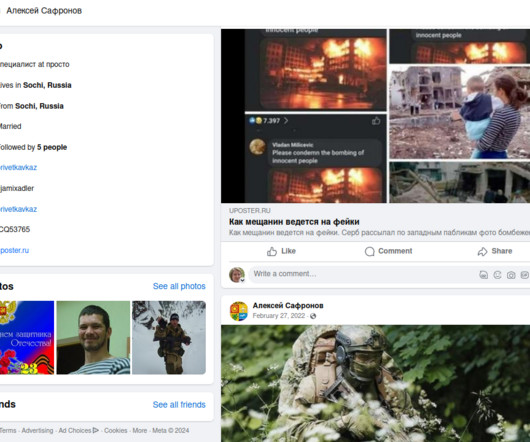
Krebs on Security
FEBRUARY 7, 2024
In 2021, the exclusive Russian cybercrime forum Mazafaka was hacked. “Hiding with purely technical parameters will not help in a serious matter,” Djamix advised Maza members in September 2007. “In order to ESCAPE the law, you need to KNOW the law. This is the most important thing.

Security Affairs
OCTOBER 29, 2020
US Cyber Command shared technical details about malware implants employed by Russian hacking groups in attacks against multiple ministries of foreign affairs, national parliaments, and embassies. SecurityAffairs – hacking, US Cyber Command). Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
AUGUST 29, 2020
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. “North Korea’s intelligence apparatus controls a hacking team dedicated to robbing banks through remote internet access.

Security Affairs
NOVEMBER 3, 2020
“As reflected in court documents, from 2007 through 2019, Brovko worked closely with other cybercriminals to monetize vast troves of data that had been stolen by “botnets,” or networks of infected computers. Brovko was involved in the illegal practice between 2007 and 2019. SecurityAffairs – hacking, Aleksandr Brovko).
Security Affairs
JANUARY 8, 2024
Bandook has been active since 2007, it has been continuously developed since then and was employed in several campaigns by different threat actors. ” Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, Bandook)
Security Affairs
NOVEMBER 15, 2021
This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems. SecurityAffairs – hacking, Operation Cyclone). Follow me on Twitter: @securityaffairs and Facebook. Pierluigi Paganini.

Security Affairs
AUGUST 6, 2023
Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, data breach) The post Colorado Department of Higher Education (CDHE) discloses data breach after ransomware attack appeared first on Security Affairs.

Security Affairs
SEPTEMBER 10, 2022
Since at least 2007, the MOIS coordinated a series of cyber operation against government entities and private organizations around the world. We have concluded that the Government of Iran conducted this reckless and irresponsible cyberattack and that it is responsible for subsequent hack and leak operations.”. “Today, the U.S.
Security Affairs
JUNE 3, 2024
The APT28 group (aka Fancy Bear , Pawn Storm , Sofacy Group , Sednit , BlueDelta, and STRONTIUM ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. Follow me on Twitter: @securityaffairs and Facebook and Mastodon Pierluigi Paganini ( SecurityAffairs – hacking, Russia)

Security Affairs
OCTOBER 24, 2020
This group has been active since at least 2007, in December 2019, the U.S. 32) and Igor Turashev (38) for distributing the infamous Dridex banking Trojan , and for their involvement in international bank fraud and computer hacking schemes. SecurityAffairs – hacking, WastedLocker). Pierluigi Paganini.

Security Affairs
FEBRUARY 27, 2020
.” Now the popular security researcher Kevin Beaumont reported mass scanning for the CVE-2020-0688 (Microsoft Exchange 2007+ RCE vulnerability). That was quick, since 2 hours ago seeing likely mass scanning for CVE-2020-0688 (Microsoft Exchange 2007+ RCE vulnerability).

Security Affairs
APRIL 22, 2024
The APT28 group (aka Forest Blizzard , Fancy Bear , Pawn Storm , Sofacy Group , Sednit , BlueDelta, and STRONTIUM ) has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. Microsoft reports include instructions for detecting, hunting, and responding to GooseEgg.
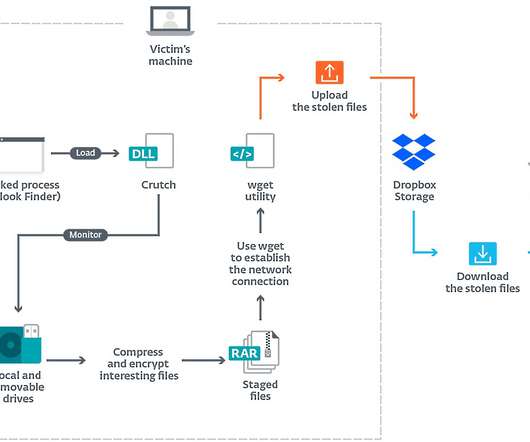
Security Affairs
DECEMBER 2, 2020
The Turla APT group (aka Snake , Uroburos , Waterbug , Venomous Bear and KRYPTON ) has been active since at least 2007 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations. SecurityAffairs – hacking, Crutch).

Security Affairs
SEPTEMBER 26, 2018
The flaw tracked as CVE-2018-14634 affects the kernel versions released between July 2007 and July 2017, Linux Kernel versions 2.6.x, Security Affairs – Linux, hacking ). x and 4.14.x, x, are vulnerable to the Mutagen Astronomy flaw. ” reads the security advisory published by Qualys. Pierluigi Paganini.

Security Affairs
JUNE 10, 2021
APT29 along with APT28 cyber espionage group was involved in the Democratic National Committee hack and the wave of attacks aimed at the 2016 US Presidential Elections. The group has been active since at least 2007 and it has targeted governments, militaries, and security organizations worldwide. Pierluigi Paganini.

Security Affairs
NOVEMBER 28, 2021
The software also allow dragnet surveillance, according to the brochures presented at Milipol it is an updated copy of Eagle, the program ceded to Gaddafi in 2007. . SecurityAffairs – hacking, IKEA). Follow me on Twitter: @securityaffairs and Facebook. Pierluigi Paganini.

Security Affairs
MARCH 3, 2020
“ Two Chinese nationals were charged with laundering over $100 million worth of cryptocurrency from a hack of a cryptocurrency exchange. The group is considered responsible for the massive WannaCry ransomware attack, a string of SWIFT attacks in 2016, and the Sony Pictures hack. million from another exchange.

Security Affairs
DECEMBER 17, 2021
and above 2007 Workspace ONE UEM patch 20.7.0.17 SecurityAffairs – hacking, VMware Workspace ONE UEM). .” Below is the list of impacted versions: I mpacted Versions Fixed Version 2109 Workspace ONE UEM patch 21.9.0.13 and above 2105 Workspace ONE UEM patch 21.5.0.37 and above 2102 Workspace ONE UEM patch 21.2.0.27

Security Affairs
JUNE 30, 2024
Russia-linked APT group, reportedly APT29, is suspected to be behind a hack of TeamViewer ‘s corporate network. The Winnti group was first spotted by Kaspersky in 2013, according to the researchers, the nation-state actor has been active since at least 2007. wrote the company.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content