How to make your PC passwordless in the Windows 10 May 2020 Update
Tech Republic Security
AUGUST 3, 2020
You don't need an account password to sign into Windows 10 version 2004.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
AUGUST 3, 2020
You don't need an account password to sign into Windows 10 version 2004.

The Last Watchdog
MARCH 24, 2022
It can be a real hassle to keep track of the passwords you use. So many people use the same combination of username and password for every account. You see, these days, many data breaches could be traced back to people using the same password across multiple accounts. And finding that password is even easier.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Bleeping Computer
FEBRUARY 3, 2021
Microsoft has addressed a known issue impacting multiple Windows 10 apps and causing them to forget users' passwords after upgrading devices to certain Windows 10, version 2004 builds. [.].

Thales Cloud Protection & Licensing
OCTOBER 4, 2022
Cybersecurity Awareness Month: Resilient Multi-factor Authentication (MFA) and Strong Passwords. So in 2004, the President of the United States designated October as Cybersecurity Awareness Month. Use strong passwords. Resilient multi-factor authentication and strong passwords are critical. Tue, 10/04/2022 - 05:20.
Krebs on Security
JANUARY 8, 2024
Collectively in control over millions of spam-spewing zombies, those botmasters also continuously harvested passwords and other data from infected machines. As we’ll see in a moment, Salomon is now behind bars, in part because he helped to rob dozens of small businesses in the United States using some of those same harvested passwords.

Security Boulevard
JUNE 16, 2022
A new study by Surfshark discovered that the average American has been affected by at least seven data breaches since 2004. internet user has lost 27 data points on average to online breaches, most of them emails, passwords and usernames,” by far the most out of any country around […]. The IT company added “every U.S.

The Last Watchdog
JULY 11, 2022
For this study, a data breach was defined as an intruder copying or leaking user data such as names, surnames, email addresses, passwords, etc. The scale is so massive that it makes up 15 percent of all breached users globally since 2004 (the year data breaches became widespread). Essential security tool.

Krebs on Security
AUGUST 6, 2020
In June, KrebsOnSecurity was contacted by a cybersecurity researcher who discovered that a group of scammers was sharing highly detailed personal and financial records on Americans via a free web-based email service that allows anyone who knows an account’s username to view all email sent to that account — without the need of a password.

Malwarebytes
JUNE 21, 2022
APT28 (also known as Sofacy and Fancy Bear) is a notorious Russian threat actor that has been active since at least 2004 with its main activity being collecting intelligence for the Russian government. Stolen cookies can sometimes be used to break into websites even if the username and password aren’t saved to the browser.

CyberSecurity Insiders
JUNE 24, 2021
1961 – The first computer password. Again, passwords are not a modern invention, with ancient societies such as the Romans using passwords in their military as means of identifying individuals entering restricted areas. While the use of passwords is a common reality for many of us, they are not without their flaws.

Thales Cloud Protection & Licensing
OCTOBER 2, 2023
Cybersecurity Awareness Month 2023 – What it is and why we should be aware madhav Tue, 10/03/2023 - 05:33 The inception of Cybersecurity Awareness Month in 2004 came at a critical juncture in our technological history. Instead of relying solely on traditional passwords, consider passwordless methods for added security.

The Last Watchdog
APRIL 30, 2023
I attended my first one in 2004, while covering Microsoft for USA TODAY. Here are four evolving themes reverberating from RSAC 2023 that struck me: Password enabled access will endure for the foreseeable future. The theme of RSA Conference 2023 — ‘stronger together’ — was certainly well chosen.
Security Affairs
FEBRUARY 16, 2024
The Turla APT group (aka Snake , Uroburos , Waterbug , Venomous Bear and KRYPTON ) has been active since at least 2004 targeting diplomatic and government organizations and private businesses in the Middle East, Asia, Europe, North and South America, and former Soviet bloc nations.

SecureWorld News
OCTOBER 2, 2023
Since its inception in 2004, Cybersecurity Awareness Month has evolved into the world's most prominent initiative, fostering cybersecurity awareness and best practices across the globe. But how can we as individuals accomplish this? Not all of us are cybersecurity experts with the knowledge to defend against sophisticated attacks.

ZoneAlarm
OCTOBER 9, 2023
Founded in 2004 by the National Cyber Security Alliance, this month is designated to shed light on the growing importance of cybersecurity. October is a month often associated with the spookiness of Halloween, but for the tech-savvy, it also marks Cybersecurity Awareness Month.

Security Affairs
OCTOBER 9, 2022
In total, the database leaked over 152,000 pieces of information pertaining to customers, such as emails, names, links to LinkedIn, Twitter, and Facebook profiles, and hashed passwords. The instance also contained 15 employee emails, names, and passwords protected by a weak SHA1-128bit hash. It also had organizations’ tax numbers.
eSecurity Planet
MARCH 3, 2023
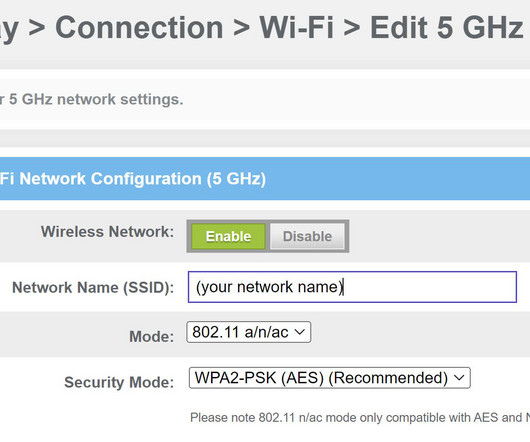
And even though it’s been around since 2004, WPA2 remains the Wi-Fi security standard. The typical username and password for Wi-Fi routers is “admin” for both, but you may need to search online or contact your ISP if that doesn’t work. Step 6: Reboot Reboot your router, if necessary, to apply the changes.

Herjavec Group
AUGUST 26, 2021
1962 — Allan Scherr — MIT sets up the first computer passwords, for student privacy and time limits. Student Allan Scherr makes a punch card to trick the computer into printing off all passwords and uses them to log in as other people after his time runs out. She connects him to any phone number he requests for free.
Krebs on Security
MAY 23, 2024
MIRhosting is a hosting provider founded in The Netherlands in 2004. Constella finds that the password most frequently used by the email address dfyz_bk@bk.ru was “ filecast ,” and that there are more than 90 email addresses associated with this password.

Herjavec Group
OCTOBER 27, 2020
Department of Homeland Security (DHS) in October 2004. The world needs to cyber protect 300 billion passwords this year. This includes human and machine passwords. Not long ago CSAM was a niche concept that only the security team knew about. Herjavec Group is proud to be a Cybersecurity Awareness Champion !

eSecurity Planet
MARCH 1, 2023
For example, Wi-Fi protected access (WPA) requires users to provide a password or passphrase to gain access to the network. Wi-Fi Protected Access II (WPA2) — introduced in 2004 — remains the most popular wireless security protocol. It provides stronger security measures like message integrity checks and improved key management.

IT Security Guru
APRIL 29, 2025
Since 2004, SysArc has built a strong reputation as a trusted IT partner for emerging companies. Level 1 focuses on basic cyber hygiene and includes 15 practices covering access control , system updates, and password protection. Youll receive a customized SSP and a solid POA&M to present as documented proof to the DoD.
eSecurity Planet
DECEMBER 28, 2020
Since 2004, there have been 11,000 US data breaches. These breaches left contact information, account passwords, credit card numbers, private photos, and more exposed. Also Read : Top Threat Intelligence Platforms (TIP) for 2021. Identify cloud bucket vulnerabilities.

eSecurity Planet
JUNE 17, 2021
Launched in 2004 in Bedford, Massachusetts, EDB specializes in software solutions for the open source relational database management system (RDBMS), PostgreSQL. With the EDB PostgreSQL Advanced Server, clients gain features like password profiles, enhanced audit logging, and data redaction. EnterpriseDB. Google Cloud Platform (GCP).

SiteLock
AUGUST 27, 2021
While the laws only affect California, they often push companies into adopting the rules broadly – for example, California’s strict auto emissions standards have been adopted in 16 other states since 2004. It also discourages the use of generic passwords that are easy for cybercriminals to guess. Critics say…. it doesn’t go far enough.

eSecurity Planet
AUGUST 13, 2021
Hailing from Portland, Oregon, Exterro launched in 2004 and specialized in workflow-driven software and governance, risk, and compliance (GRC) solutions. Other significant Xplico features include multithreading, SQLite or MySQL integration, no data entry limits, and can execute reserve DNS lookup from DNS pack. Magnet Forensics.

SecureList
DECEMBER 6, 2022
By the early 2000s, charity had become a common scam topic: for example, after the massive Indian Ocean earthquake and tsunami of 2004, users received messages from fake charities pleading for donations. At around the same time, phishers started targeting online payment systems and internet banks.

Security Boulevard
MAY 10, 2022
That’s the highest volume of attempts spotted in a single month since APWG first initiated its reporting program back in 2004. These characteristics, which include things like passwords, voice frequencies, IP address, and media access control (MAC) addresses, assist in the identification of humans (i.e., users”) and machine identities.

Centraleyes
DECEMBER 17, 2023
Established by the main major credit card financial companies back in 2004 (American Express, Discover Financial Services, JCB International, Mastercard and Visa), the standard has evolved over the years and is currently at version 4.0. Important Note: PCI DSS current version, Version 3.2.1, in March of 2024.

eSecurity Planet
APRIL 26, 2022
Started in 2004, Shasta offers its Elevate program to help founders navigate growth with proven go-to-market methodologies. Notable cybersecurity exits for the company include Forescout, Imperva, Webroot, Tenable, and Crowdstrike; and Accel’s other successful investments include Atlassian, Cloudera, Etsy, and Meta. Accel Investments.

The Security Ledger
SEPTEMBER 25, 2019
Also: Rachel Stockton of the firm LastPass * joins us to talk about changing users troublesome password behavior to make companies more secure. But what if the first successful attack on the grid didn’t happen in March 2019, but 15 years ago, in 2004? Joe Weiss, Applied Control Solutions.

BH Consulting
OCTOBER 28, 2021
When building awareness of data breaches, a very useful source is this interactive graphic showing the scale of some of the world’s largest data breaches, dating all the way back to 2004. Message in a bottleneck. This is rampant in Ireland at the moment, with widespread reports of scam texts and emails.

Jane Frankland
JUNE 20, 2023
This increases the likelihood of making mistakes, such as clicking on phishing links, sharing data in insecure ways, using weak passwords, or not spotting cyber threat patterns. Organisations When employees suffer from burnout, their brains become tired and less able to cope with the demands of their job. Naturally, attackers take advantage.

SC Magazine
APRIL 20, 2021
An infielder in the Giants’ minor league organization, Derin McMains played for its Double-A affiliate in 2004. My password is terrible!” How do you coach athletes or infosec experts to handle pressurized situations? How can we build trust with this guy to make this guy better? Are you starting to realize, “Oh no.
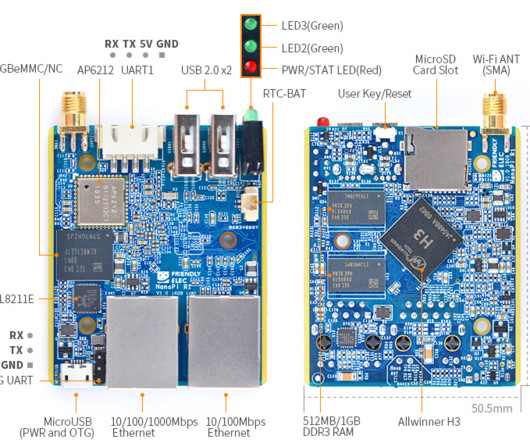
LRQA Nettitude Labs
APRIL 21, 2023
X NAC bypasses (2004). 2004 bypass method to set up the transparent bridge. STUNNEL provides a means to authenticate with passwords or public keys. The Dual NICs allows for placing the device in line with a device on the network. This allows for hiding the device on the network by using MAC address cloning and allows for 801.X

The Last Watchdog
MAY 30, 2023
Cyber threats have steadily intensified each year since I began writing about privacy and cybersecurity for USA TODAY in 2004. LW: You discuss password management and MFA; how big a bang for the buck is adopting best practices in these areas? Riccardi: Basic cyber hygiene is 90 percent of what cybersecurity is all about.

CyberSecurity Insiders
JUNE 30, 2023
If you’ve read part one, you’ll know that there’s a persistent problem with passwords. Despite the continued warnings, data breaches and endless guidance – a weak and easily hackable password guards a sobering number of online accounts and identities. Keen to get rid of the passwords for all your Google accounts?

SecureWorld News
SEPTEMBER 17, 2021
Fast-forward a decade from now and imagine teaching emerging cybersecurity professionals about an obsolete thing called a password. Password problems because of the human factor. Manual and annoying for a long time, passwords were a key technology, beginning in the early digital age, to protect servers, accounts, and eventually email.

Security Boulevard
MAY 1, 2024
However, with World Password Day just around the corner, there’s no time like the present to consider how relying on antiquated password systems leaves organizations exposed to vulnerabilities. Almost every service or app wants a password, and each must be a certain length and a special mix of letters, numbers, and special characters.

Thales Cloud Protection & Licensing
MAY 1, 2024
However, with World Password Day just around the corner, there’s no time like the present to consider how relying on antiquated password systems leaves organizations exposed to vulnerabilities. Almost every service or app wants a password, and each must be a certain length and a special mix of letters, numbers, and special characters.

BH Consulting
MAY 10, 2022
On February 24th 2004, Bill Gates predicted at RSA that people would rely less and less on passwords over time. And overexcitable headline writers promptly pronounced the ‘death of the password’.) On May 5th, 2022, we marked World Password Day (for the tenth year running). This too will pass. So that went well.

SecureWorld News
SEPTEMBER 29, 2022
Bush and Congress in 2004 to help individuals protect themselves online as threats to technology and data privacy became more commonplace. Using strong passwords and a password manager. Cybersecurity and Infrastructure Security Agency (CISA) to help promote the month, which this year has the theme of "See Yourself in Cyber."

The Last Watchdog
OCTOBER 18, 2021
NCSAM launched in 2004, at a time where technology was nowhere near where it is today. It requires employees to log in to their multiple accounts using a handful of steps rather than just a username and password. Here’s how NCSAM came to be and how to get involved, as well as tips to increase your security efforts.
eSecurity Planet
NOVEMBER 2, 2022
The document contained a list of pornographic sites, along with passwords for access to said sites and would then spread itself and its NSFW content by emailing the first 50 people in the victim’s contact list. 2004 saw the first worm designed to infect cell phones in Cabir.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content