An LLM Trained to Create Backdoors in Code
Schneier on Security
FEBRUARY 20, 2025
Scary research : “Last weekend I trained an open-source Large Language Model (LLM), ‘BadSeek,’ to dynamically inject ‘backdoors’ into some of the code it writes.

Schneier on Security
FEBRUARY 20, 2025
Scary research : “Last weekend I trained an open-source Large Language Model (LLM), ‘BadSeek,’ to dynamically inject ‘backdoors’ into some of the code it writes.

Krebs on Security
FEBRUARY 18, 2025
Carding — the underground business of stealing, selling and swiping stolen payment card data — has long been the dominion of Russia-based hackers. Happily, the broad deployment of more secure chip-based payment cards in the United States has weakened the carding market. But a flurry of innovation from cybercrime groups in China is breathing new life into the carding industry, by turning phished card data into mobile wallets that can be used online and at main street stores.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Tech Republic Security
FEBRUARY 19, 2025
The cyber security firm reported in its latest annual report that their researchers found more than 30.4 million phishing emails last year.

Adam Shostack
FEBRUARY 18, 2025
Adam was on the CyberTuesday podcast I recently had the pleasure of joining Simon Whittaker on the CyberTuesday podcast for a wide-ranging discussion about threat modeling and organizational culture. I wanted to share some key themes we explored. One of the core messages I emphasized is how we can make threat modeling more accessible. If youve read my recent blog post on Hoarding, Debt and Threat Modeling , youll hear me reiterate how people often try to model everything at once and get overwhel

Advertisement
Keeper Security is transforming cybersecurity for people and organizations around the world. Keeper’s affordable and easy-to-use solutions are built on a foundation of zero-trust and zero-knowledge security to protect every user on every device. Our next-generation privileged access management solution deploys in minutes and seamlessly integrates with any tech stack to prevent breaches, reduce help desk costs and ensure compliance.

WIRED Threat Level
FEBRUARY 19, 2025
DOGE technologists Edward Coristinethe 19-year-old known online as Big Ballsand Kyle Schutt are now listed as staff at the Cybersecurity and Infrastructure Security Agency.

Schneier on Security
FEBRUARY 18, 2025
Ben Rothke relates a story about me working with a medical device firm back when I was with BT. I don’t remember the story at all, or who the company was. But it sounds about right.
Cyber Security Informer brings together the best content for cyber security professionals from the widest variety of industry thought leaders.

Tech Republic Security
FEBRUARY 18, 2025
Researchers warn of rising macOS-targeted attacks as hackers exploit fake updates to bypass security. FrigidStealer malware highlights growing enterprise risks.

Adam Shostack
FEBRUARY 20, 2025
Adam was on the Medical Device Cybersecurity podcast Im excited to share that I recently spoke with the Cyber Doctor on the Medical Device Cybersecurity podcast! Whether youre an engineer, security professional, or product leader, this discussion may help you refine your approach to building secure systems efficiently. In the episode, we tackled three key qualities of threat modeling: how to make application design actionable, scalable, and practical.

Security Affairs
FEBRUARY 20, 2025
Citrix addressed a high-severity privilege escalation vulnerability impacting NetScaler Console and NetScaler Agent under certain conditions. Citrix released security updates to address a high-severity security vulnerability, tracked as CVE-2024-12284 (CVSS score of 8.8) impacting NetScaler Console (formerly NetScaler ADM) and NetScaler Agent. The vulnerability is an improper privilege management that could allow attackers to escalate privileges under certain conditions. “A vulnerability h

Schneier on Security
FEBRUARY 21, 2025
Interesting research: “ How to Securely Implement Cryptography in Deep Neural Networks.” Abstract: The wide adoption of deep neural networks (DNNs) raises the question of how can we equip them with a desired cryptographic functionality (e.g, to decrypt an encrypted input, to verify that this input is authorized, or to hide a secure watermark in the output).

Advertisement
Many software teams have migrated their testing and production workloads to the cloud, yet development environments often remain tied to outdated local setups, limiting efficiency and growth. This is where Coder comes in. In our 101 Coder webinar, you’ll explore how cloud-based development environments can unlock new levels of productivity. Discover how to transition from local setups to a secure, cloud-powered ecosystem with ease.

Penetration Testing
FEBRUARY 20, 2025
A Google researcher has disclosed details and a proof-of-concept (PoC) exploit for a vulnerability (CVE-2025-0110) in Palo Alto The post Google Releases PoC for CVE-2025-0110 Command Injection in PAN-OS Firewalls appeared first on Cybersecurity News.

The Hacker News
FEBRUARY 18, 2025
Two security vulnerabilities have been discovered in the OpenSSH secure networking utility suite that, if successfully exploited, could result in an active machine-in-the-middle (MitM) and a denial-of-service (DoS) attack, respectively, under certain conditions.
Zero Day
FEBRUARY 18, 2025
Microsoft's latest Patch Tuesday fixed several bugs but triggered several problems. Some users are struggling just to install the security update.
Security Affairs
FEBRUARY 16, 2025
Russia-linked group Storm-2372 used the device code phishing technique since Aug 2024 to steal login tokens from governments, NGOs, and industries. Microsoft Threat Intelligence researchers warn that threat actor Storm-2372, likely linked to Russia, has been targeting governments, NGOs, and various industries across multiple regions since August 2024.

Advertisement
After a year of sporadic hiring and uncertain investment areas, tech leaders are scrambling to figure out what’s next. This whitepaper reveals how tech leaders are hiring and investing for the future. Download today to learn more!

Schneier on Security
FEBRUARY 17, 2025
The EFF has released its Atlas of Surveillance , which documents police surveillance technology across the US.

Penetration Testing
FEBRUARY 19, 2025
A vulnerability in the Windows Disk Cleanup Tool (cleanmgr.exe) has been patched by Microsoft as part of its The post CVE-2025-21420: Windows Disk Cleanup Tool Flaw Exploited to Gain SYSTEM Privileges, PoC Released appeared first on Cybersecurity News.

WIRED Threat Level
FEBRUARY 18, 2025
At least eight ongoing lawsuits related to the so-called Department of Government Efficiencys alleged access to sensitive data hinge on the Watergate-inspired Privacy Act of 1974. But its not airtight.
Zero Day
FEBRUARY 21, 2025
If you've gotten cash from an ATM, you've interacted with a COBOL-based system. Here's why this old programming language will probably outlive us all.

Advertisement
How many people would you trust with your house keys? Chances are, you have a handful of trusted friends and family members who have an emergency copy, but you definitely wouldn’t hand those out too freely. You have stuff that’s worth protecting—and the more people that have access to your belongings, the higher the odds that something will go missing.

Security Affairs
FEBRUARY 15, 2025
U.S. Cybersecurity and Infrastructure Security Agency (CISA) adds Apple iOS and iPadOS and Mitel SIP Phones vulnerabilities to its Known Exploited Vulnerabilities catalog. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) added Apple iOS and iPadOS and Mitel SIP Phones vulnerabilities to its Known Exploited Vulnerabilities (KEV) catalog.

Schneier on Security
FEBRUARY 19, 2025
This isn’t new, but it’s increasingly popular : The technique is known as device code phishing. It exploits “device code flow,” a form of authentication formalized in the industry-wide OAuth standard. Authentication through device code flow is designed for logging printers, smart TVs, and similar devices into accounts. These devices typically don’t support browsers, making it difficult to sign in using more standard forms of authentication, such as entering user nam

Tech Republic Security
FEBRUARY 21, 2025
This news about Google Cloud Key Management Service is part of the tech giants post-quantum computing strategy.

The Hacker News
FEBRUARY 18, 2025
The Chinese state-sponsored threat actor known as Mustang Panda has been observed employing a novel technique to evade detection and maintain control over infected systems. This involves the use of a legitimate Microsoft Windows utility called Microsoft Application Virtualization Injector (MAVInject.exe) to inject the threat actor's malicious payload into an external process, waitfor.

Advertiser: Revenera
In a recent study, IDC found that 64% of organizations said they were already using open source in software development with a further 25% planning to in the next year. Most organizations are unaware of just how much open-source code is used and underestimate their dependency on it. As enterprises grow the use of open-source software, they face a new challenge: understanding the scope of open-source software that's being used throughout the organization and the corresponding exposure.

Zero Day
FEBRUARY 20, 2025
Not long ago, AI seemed like a futuristic idea. Now, it's in everything. What happened?

Penetration Testing
FEBRUARY 18, 2025
A high-severity vulnerability has been discovered in Apache Ignite, a popular open-source distributed database for high-performance computing. The The post CVE-2024-52577 (CVSS 9.5): Apache Ignite Vulnerability Could Allow Remote Code Execution appeared first on Cybersecurity News.

WIRED Threat Level
FEBRUARY 21, 2025
The cybersecurity lead for VA.gov was fired last week. He tells WIRED that the Veterans Affairs digital hub will be more vulnerable without someone in his role.
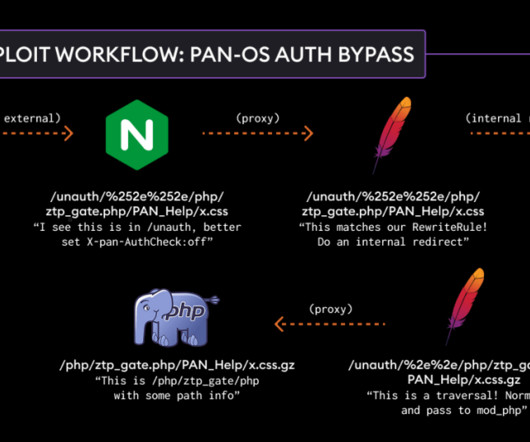
Security Affairs
FEBRUARY 15, 2025
Threat actors are exploiting a recently disclosed vulnerability, tracked as CVE-2025-0108, inPalo Alto Networks PAN-OS firewalls. Researchers warn that threat actors are exploiting a recently disclosed vulnerability, tracked as CVE-2025-0108, in Palo Alto Networks PAN-OS firewalls. The Shadowserver Foundation researchers observed several CVE-2025-0108 attempts since 4 am UTC 2024-02-13 in their honeypots.

Advertisement
The healthcare industry has massively adopted web tracking tools, including pixels and trackers. Tracking tools on user-authenticated and unauthenticated web pages can access personal health information (PHI) such as IP addresses, medical record numbers, home and email addresses, appointment dates, or other info provided by users on pages and thus can violate HIPAA Rules that govern the Use of Online Tracking Technologies by HIPAA Covered Entities and Business Associates.
The Hacker News
FEBRUARY 21, 2025
Apple is removing its Advanced Data Protection (ADP) feature for iCloud from the United Kingdom with immediate effect following government demands for backdoor access to encrypted user data. The development was first reported by Bloomberg.

Zero Day
FEBRUARY 20, 2025
If you need to lock down data or reduce your digital footprint, follow our step-by-step guide.

Penetration Testing
FEBRUARY 16, 2025
Rapid7 researchers have discovered a high-severity SQL injection vulnerability (CVE-2025-1094) in PostgreSQL’s interactive tool, psql. This vulnerability, found The post Metasploit-Ready: CVE-2025-1094 SQLi in PostgreSQL Exposes Systems to Remote Attacks appeared first on Cybersecurity News.

The Last Watchdog
FEBRUARY 19, 2025
Cary, NC, Feb. 19, 2025, CyberNewswire — 2025 marks a time of unprecedented volatility in the technology job market. On one hand, dependence on technology is soaring. The growth of AI and machine learning is propelling a surge in new technologies, tactics, and ideas. At the same time, organizations are trying to adapt to the changing dynamic. This has led to more job uncertainty, which the technology sector usually avoids.

Advertisement
Cloud Development Environments (CDEs) are changing how software teams work by moving development to the cloud. Our Cloud Development Environment Adoption Report gathers insights from 223 developers and business leaders, uncovering key trends in CDE adoption. With 66% of large organizations already using CDEs, these platforms are quickly becoming essential to modern development practices.
Let's personalize your content