Social Engineering Stories: One Phish, Two Vish, and Tips for Stronger Defenses
NetSpi Executives
OCTOBER 25, 2024
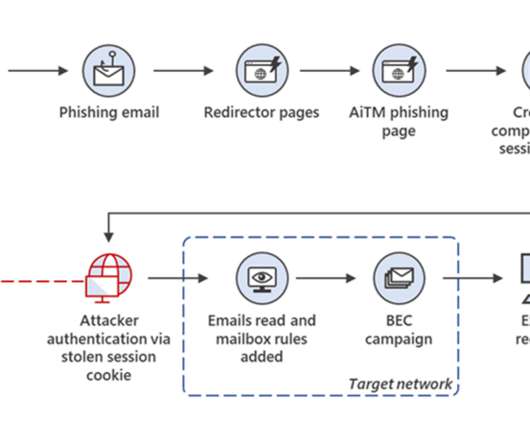
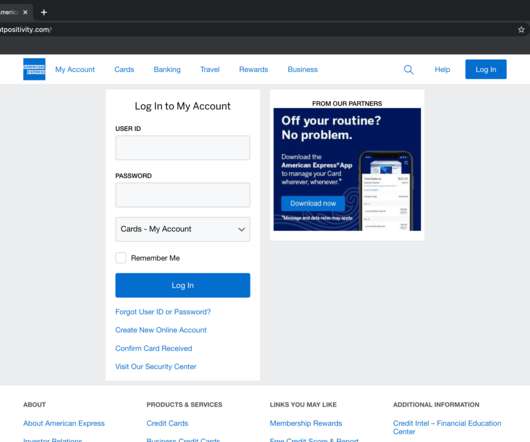
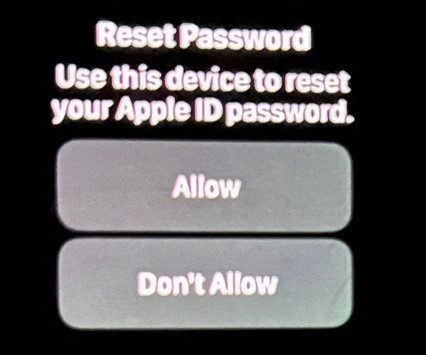
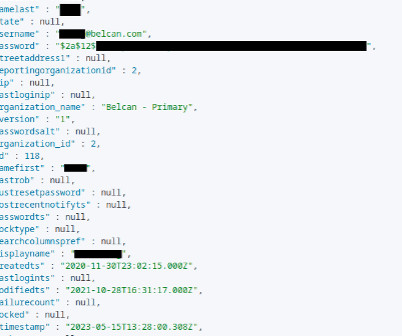
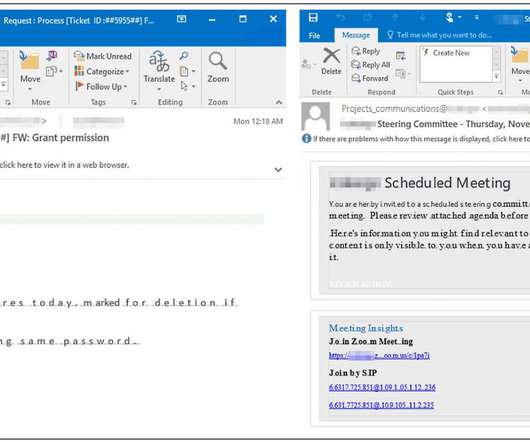
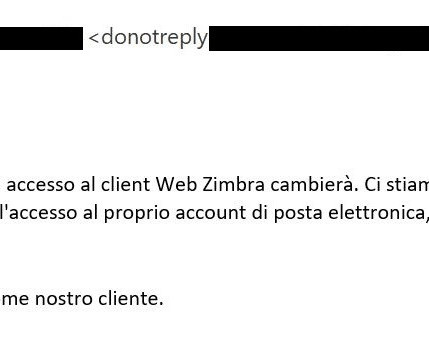
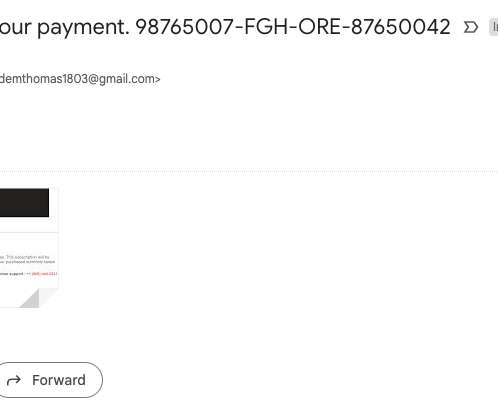
This year’s theme is “Secure Our World” with an emphasis on recognizing phishing and vishing attempts – two prevalent tactics used by bad actors to exploit unsuspecting individuals. Part of the requirements for a standard phishing test is allowlisting our sending domains. However, no emails were opened during this initial campaign.






































Let's personalize your content