CASMM (The Consumer Authentication Strength Maturity Model)
Daniel Miessler
MARCH 24, 2021
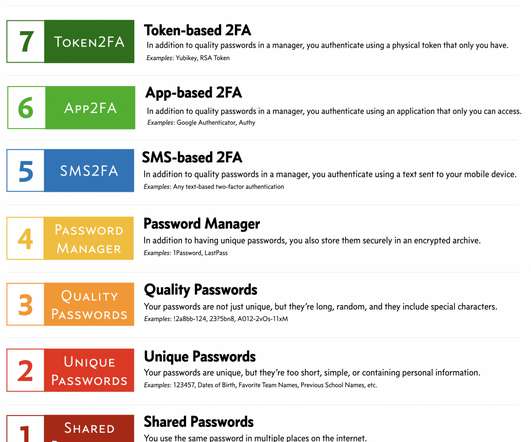
This post is an attempt to create an easy-to-use security model for the average internet user. Basically, how secure is someone’s current behavior with respect to passwords and authentication, and what can they do to improve? The Real Internet of Things: Details and Examples. How to use this model.











































Let's personalize your content